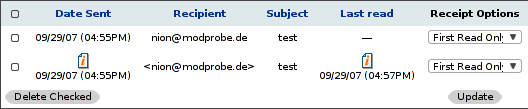
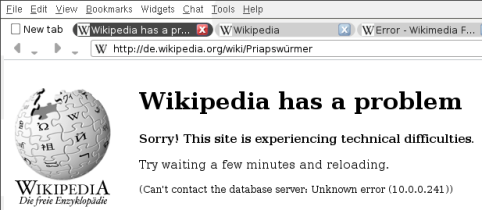
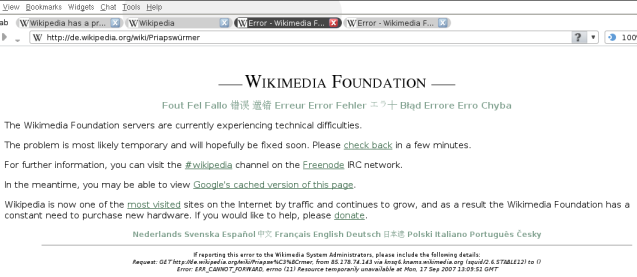
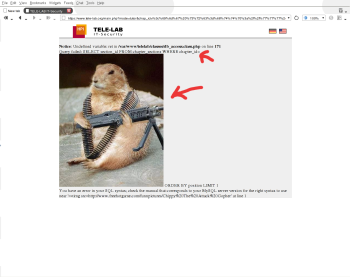
Entries tagged as www
annouce awards data mining debian dns google hacking information knowledge opera privacy release search engines security software sofware web apache block config fail2ban spam trackback april filesharing flame jokes news piratebay random blurb darwin net culture nonsense pwnage theory bill fun browser javascript netscape wtf bugmenot retailmenot bugs argh code dsa esr fetchmail frustration heise ntp ouch php rant releases suhosin censorship flickr web 2.0 acpi announce apple bash c cli file system functions hacks hardware ipod libacpi linux programming reverse scripts service shell stfl text mode tools yacpi zsh comics dilbert flashsucks comments fefe community grml wikipedia build chroot documentation dpkg eyecandy filesystem mutt network networking scponly setup sftp ssh tests text tools tip tips troubleshooting user fail xing archlinux art blogging conferences configuration convtroversy copyright debconf distributions distributors dpl eeepc errm errm? feature fix fud gcc gpl graphs icecast im images installation keysigning kudos leader libs licenses maemo meetings mpd music n900 newsbeuter nitrogen notebook open source openbox openoffice packages pary patches podcast project qa review rss scripting squeeze streaming stuff toy story ubuntu vim.editing wallpaper websites xinerama 911 commands conspiracy gsm howto links mobile phones phrack power protocols sus truth unix dotcom email advertising monitoring strato sucks tracking webhosting adobe irc ssl analysis backdoor events itb omg phone sms specs vendors youtube faq w3c web security feed reader insults misc net firefox linuxtag cinema critics dhl films games hurd internet iptables movie myths pizza telnet ups video voting machines passwords phishing live cd survey 25c3 ccc congress companies ctf flagseverywhere pain radare tricks 23c3 binary cracking hex ii noos wordpress 9/11 toll collect wikileaks applications archive arm cities conference copy&paste dell europe exploit features femtocell fosdem graphics kernel munin ncurses openwrt paper presentation problems rms rsync services sfr solutions suspend terminal uberguru ubiquisys compiler optimization pidgin testing biometry burger cool stuff food it crowd personal season 2 series soap stop-motion telephone random thoughts xss pdf pwsafe alerts attacks compromises dos exim gpg key transition mail mobile osmocombb pgp driver fglrx help lazyweb partnership
Calendar

|
November '15 | |||||
| Mon | Tue | Wed | Thu | Fri | Sat | Sun |
| 1 | ||||||
| 2 | 3 | 4 | 5 | 6 | 7 | 8 |
| 9 | 10 | 11 | 12 | 13 | 14 | 15 |
| 16 | 17 | 18 | 19 | 20 | 21 | 22 |
| 23 | 24 | 25 | 26 | 27 | 28 | 29 |
| 30 | ||||||
Quicksearch
Support
Recent Entries
- E-Plus GSM privacy/TMSI allocation leak
- Thursday, October 11 2012
- Exploiting the Ubiquisys/SFR femtocell webserver (wsal/shttpd/mongoose/yassl embedded webserver)
- Wednesday, August 3 2011
- So what happened recently...
- Wednesday, April 6 2011
- Sunday, February 6 2011
- exim remote vulnerability
- Thursday, December 9 2010
- Will my Phone Show An Unencrypted Connection?
- Wednesday, September 8 2010
- smpCTF 2010 quals writeups
- Sunday, August 8 2010
- protocol design fail: MMS notification
- Wednesday, July 28 2010
- acrobat reader stealing my passwords
- Tuesday, June 29 2010
- UnrealIRCd backdoored
- Saturday, June 12 2010
Categories
Tag cloud
23c3 acpi advertising annouce announce april argh art awards bash blogging bugs c cli code conferences config configuration data mining debconf debian dell dns documentation email errm? events exploit fail fail2ban filesharing films flame fun gcc google graphs grml gsm hacking hacks hardware heise images information installation internet irc knowledge libacpi links linux mobile phones network news newsbeuter omg open source opera passwords php power privacy programming qa random blurb rant release releases rss scripts security service setup shell sms software spam ssh stfl stuff terminal tests text mode tip tips tools troubleshooting unix user video vim.editing web web 2.0 websites wordpress wtf www youtube zsh