Posted by Nico Golde in
Wednesday, June 9. 2010
I occasionally make use of the report function in opera in case it crashes (which happens quite often on 64bit for me), but if it crashes right when receiving the response
of the crash reporting website you really start to HATE that piece of software.
(notice Last visited URL)
FAIL! (using 0.60-6351)
Posted by Nico Golde in
Wednesday, May 26. 2010
fail2ban is used by many people to prevent certain types of DoS attacks. I use it myself to reduce trackback spam a little bit.
While this tool becomes quite handy in such situations it is also not generally recommend because you can shoot yourself in the foot. If one of the used filters has a bug and results in incorrect parsing your fail2ban installation might end up banning arbitrary IP addresses or even your own IP range (not even mentioning IP spoofing).
There existed at least two bugs of this kind to my knowledge and since regex might not always be easy I'm sure there will be more in the future.
Since I didn't want to look for a specific regex bug in one of the filters I thought about IP spoofing again and looked at fail2bans filters. What I needed was a filter processing log entries of a service listening on a UDP socket as TCP/IP spoofing over the internet doesn't really work well these days. Finding such a filter would mean an instant win situation. To my surprise there is such a filter: config/filter.d/named.conf
This filter is used to parse log entries consisting of denied DNS queries produced by bind. Interestingly there is even an article at debian-administration describing how to setup fail2ban to mitigate a DNS DDoS attack. This is of course a bad idea and I have no idea why this filter is shipped in a default fail2ban installation. DoSing abritary IP addresses with this filter in use becomes as easy as firing up scapy and querying the server with a forged source IP:
>>> send(IP(dst="81.169.172.197",src="xx.46.63.71")/UDP()/DNS(rd=1,qd=DNSQR(qname="foao.modprobe.de")))
.
Sent 1 packets.
This ends up as:
May 26 22:32:22 modprobe named[30245]: client xx.46.63.71#53: query 'foao.modprobe.de/A/IN' denied
in the bind logs which in turn results in:
2010-05-26 22:32:05,551 fail2ban.actions: WARNING [named-refused] Ban xx.46.63.71
In this example the spoofed IP was xx.46.63.71 which is not under my control.
Mission statement: don't use fail2ban unless you really want to shoot yourself in the foot or know pretty well what you're doing 
Posted by Nico Golde in
Friday, March 19. 2010
It is possible with s9y to moderate blog comments after a certain amount of time has passed since the article was published.
A while back I got the following mail to approve a blog comment (I stripped the url and email address to not support the spam): Mon, 19 Oct 2009 12:18:02 +0200 (CEST)
A new comment has been posted on your blog "nion's blog", to the entry entitled "security of scponly/sftp-server in combination with apache".
Link to entry: http://nion.modprobe.de/blog/archives/679-security-of-scponlysftp-server-in-combination-with-apache.html
Requires review: Yes (Auto-moderation after X days)
User IP-address: 24.123.215.XXX
User Name: SomeSpammer
User Email: webmaster@somespammer.com
User Homepage: http://www.somespammer.com
Comments:
Very interesting, seems so simple when you explain it like that.. nice one
This is quite obviously a spam comment to increase google ranks or site links in general.
Today I got a new comment:
Fri, 19 Mar 2010 02:35:54 +0200 (CEST)
A new comment has been posted on your blog "nion's blog", to the entry entitled "security of scponly/sftp-server in combination with apache".
Link to entry: http://nion.modprobe.de/blog/archives/679-security-of-scponlysftp-server-in-combination-with-apache.html
Requires review: Yes (Auto-moderation after X days)
User IP-address: 96.30.18.XXX
User Name: SomeSpammer
User Email: webmaster@somespammer.com
User Homepage: http://www.somespammer.com/
Comments:
Weird.. I found myself back here! small world. Reminds of this one from the commmandline kung fu of wietse.
( ( mkfifo ~/nc-feef && ( ( nc -v -l -p 22123 127.0.0.1 > ~/out ) & ) && ( ( cat /tmp/ncf | nc 127.0.0.1 22123 ) & ) && script -f ~/nc-feef ) & )
This comment is pointing to the same spammer site. Now comparing this comment to the first one at the first glance it seems even related to the blog post! Thinking of "wietse" the name Wietse Venema (author of postfix) pops up, so this also familiar.
Though opening a fifo in the home directory, a netcat listening tcp port on localhost with the output redirected to a file and then some tmp file piped to the listening port (thus writing the file) and attaching script to the FIFO doesn't really make sense?! Not that this is usually the case with spam, but wtf this is everything but obviously spam. If you have a blog that is commented highly frequent it might be a problem to sort that out and spot that even if it's not interesting to you. This is the difference to email, if it's spam, you don't notice but it's also not interesting you will just delete the mail. Using a blog you might approve such a comment as it might be interesting for another reader and you don't have time to read that in detail.
So this spam hit me 6 months after the first attempt again! It's interesting to see how spam evolves over time, this one clearly has been improved.
Now spam bots are producing code. This is scary. It will be interesting to see if and what comment I get from the guy on this article 
Posted by Nico Golde in
Wednesday, March 17. 2010
... or you search for int main(int argn, char **argc) (I was looking for source code snippets that do not use the typical int argc, char **argv names) the google code search behaves rather strangely.
The first result you get is:

this is not too surprising as the google code search features regexes and * is a reserved symbol in POSIX extended regular expressions but at least the recommendation of int argn, char "main(int" "**argc)" is a bit surprising.
Searching for this actually results in a function that matches the string you wanted to search for originally. So far so good, I didn't look into the codesearch syntax in detail, so this might make sense.
The result looks like:
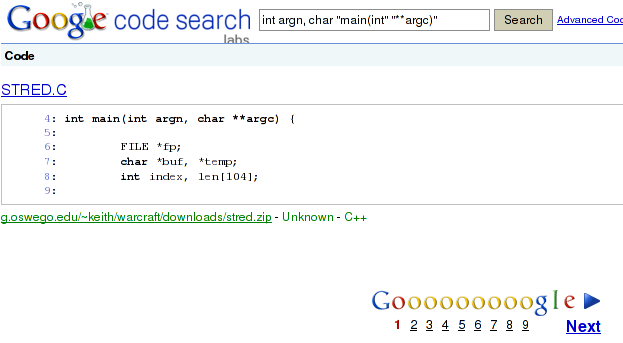
i
Note that the result has 9 pages (the screenshot is missing this detail) but also only 9 results. The first question that arises is: Why do they only display one result on the page instead of n (usually they do display more)?
Looking at the other pages it becomes confusing. On page 2 this looks like:
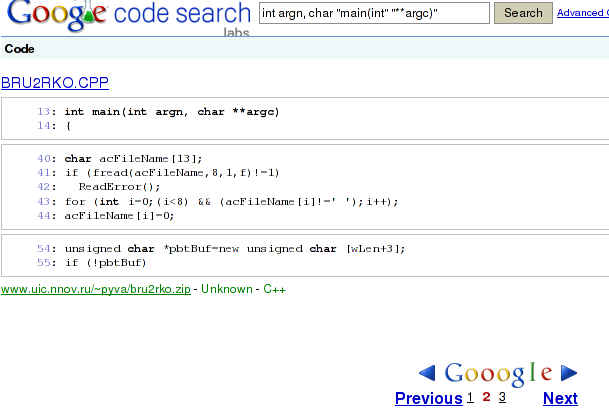
Now where have pages 4-9 been gone? Ok, to be fair, google sometimes strips additional search results if the content is too similar, this is not too surprising.
But then, visiting page 3 you get:
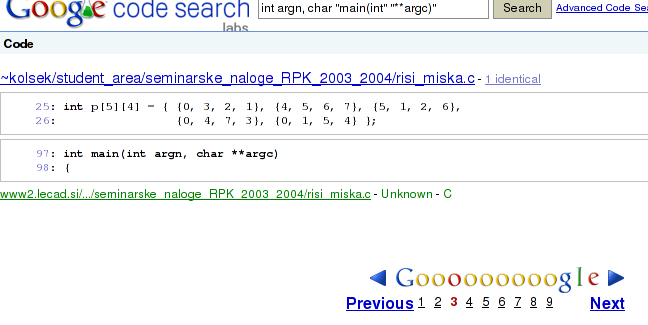
Tada, pages are there again! 
At this point I am/was totally confused and am really wondering what the idea behind this behaviour is.
If someone is using the google codesearch more frequently (or even is a google employer) please enlighten me! 
Posted by Nico Golde in
Monday, February 8. 2010
Two weeks ago I got myself a nokia n900 phone which is running maemo 5. So far I am quite happy with it, given that my previous phone was a sony erricsson p1i which is pretty crappy.
I've taken some notes about my experiences:
- under normal use the battery lasts for ~ 2 days, if I'm using 3G the whole day I need to recharge it daily though
- the terminal has a bug which results in the enter key not working under some conditions, ctrl-m works as a workaround though
- playing normal dvdrips in mplayer is absolutely no problem without downscaling, 720p doesn't perform though
- I somehow managed that my screen flipped and I wasn't able to flip it back, only a reboot solved that
- It is not clear to me which tools you will find in the list of installable packages and which are only visible with apt-cache search. I also managed to end up with a doubled launch icon in my application list for some application
- the termininal is not usable anymore after an ncurses program crashed, "reset" doesnt help either
- wireless uses less battery than umts, way less
- the back button in the browser is per default opening a fancy eyecandy browse history which is slow, so I mostly use backspace to browse back
- there is lots of useful tools in the extras-devel repository, e.g. I can control my mpd via mmpc from the phone which is great
- importing contacts works flawlessly, also merging existing contacts works as expected
- jabber (including xmpp calls) are integrated in the contacts information (you can merge a jabber uid into an existing contact)
- i've no idea yet what the internal video player is, but i wasn't able to play a non downscaled XviD file with it, mplayer does play it fine
- freely placeable widgets are awesome
- it's is really userfriendly and no geeky linux user phone
- i would prefer not having busybox per default, i can install bash but the libc is still from busybox which implies world readable password hashes in /etc/passwd, so no other user accounts on my mobile

- is there disk encryption available?
- n900fly can't cause any good

- gps with nokia maps is ok and I find it pretty usable even if a google maps client would be nice as well
- the mp3 mplayer sucks unless you have tagged your music properly, you can't just play some folder without having a playlist for it
- mplayer as an alternative from the console is no real alternative either, if you don't redirect its output to /dev/null it gets stuck in a loop when the display blanks,
- app manager locks dpkg lock even if you just list available programs, no idea why this is needed and no idea how aptitude and synaptic are doing this
- is there a good todo manager which comes with a widget listing todos?
- is it possible to install armel debian packages without having a debian chroot?
- sms are nicely organized per contact in an instant messaging fashion
- the builtin accelerator works nice and you can automatically flip the screen when you want to dial a number, sometimes happens by accident though
- the multiuser support works awesome and you get a nice overview of open applications in a composť fashion, it may be wise to have not 40 applications open though
- the list of processes is already huge (like 160 processes running in the background)
- i haven't checked out the sdk yet but I will do that soon as I need e.g. newsbeuter for RSS
- hardware feels robust, arm cortex a8 is imho a very good processor, RAM could be more (the phone is heavily swapping)
- you can not yet use the phone as a wireless access point without building your own kernel images, some people seem to be working on this
- you can manipulate all kinds of stuff through the sysfs, including the phone led and the vibration

- wireless certificates are sometimes shown to be invalid but there there is no details button, you can click only "done"
Those are the things I came up with while using the phone. The calling functionality and everything which is only phone related really works fine and the sound quality while talking to someone on the phone is also really good. So far I am really happy with the phone and I can only recommend it. I hope I'll have some time to port some applications to maemo soon.
Posted by Nico Golde in
Wednesday, December 23. 2009
I always hated garden gnomes and was under the impression that only old people collect them. But I have to realize that I just discovered the love to garden gnomes when I saw the Noam Chomsky garden gnome.
 http://www.justsaygnome.net/gnomes-noams--oms---products---ordering.html
http://www.justsaygnome.net/gnomes-noams--oms---products---ordering.html
If you ever feel like sending me a gift, send me one of those 
Too bad there's also a bunch of other important people I would like to as garden gnomes! If there is a business around that please leave a comment.
Posted by Nico Golde in
Thursday, November 26. 2009
From 3AM on Wednesday November 25, 2009, until 3AM the following day (US east coast time), WikiLeaks released half a million US national text pager intercepts. The intercepts cover a 24 hour period surrounding the September 11, 2001 attacks in New York and Washington.
The messages were broadcasted "live" to the global community — sychronized to the time of day they were sent. The first message was from 3AM September 11, 2001, five hours before the first attack, and the last, 24 hours later.
Text pagers are usualy carried by persons operating in an official capacity. Messages in the archive range from Pentagon, FBI, FEMA and New York Police Department exchanges, to computers reporting faults at investment banks inside the World Trade Center
Wow, this is an interesting release! I am not yet sure if I completely like it as it probably also carries a lot information that is not in the public interest and maybe shouldn't be public but nonetheless it is interesting to see this.
More info on: http://911.wikileaks.org/ ( index).
This in combination with the release of the Toll Collect contracts really made my day. Thanks wikileaks! You are doing a great job!
Posted by Nico Golde in
Sunday, November 22. 2009
Just a short note, I am still alive  Just being very busy with my studies and certain aspects in real life.
But there is a thing I really would like to share now and that is an attempt to visualize the Mandelbrot set in 3D. I haven't seen something like that before but it is really awesome.

The story behind that and lots of interesting pictures at: http://www.skytopia.com/project/fractal/mandelbulb.html
Posted by Nico Golde in
Thursday, October 29. 2009
A lot of people used to configure their ssh servers to listen to a port different from 22 to prevent their logs getting filled with login attempts by script kiddies. I just stumbled over sslh which is a very nice alternative to that in case you have a webserver running which supports ssl. sslh is also a good choice if you are behind a corporate firewall and ssh is filtered while SSL is probably not (and this is simpler than tunneling).
The idea is pretty simple but cool. The daemon listens on port 443 and depending on whether the client has written something into the socket (SSL) or not (SSH) after connecting the daemon "forwards" the connection to the listening service running on the same host. In case of SSL/HTTPS the client will send a request after the handshake and in case of ssh it won't. Pretty simple. I just did a quick test on one of my hosts and it seems to work great. The tool is written in C, consists of < 500 SLOC and the code looks clean to me. If you're using Debian you can just apt-get install it.
Posted by Nico Golde in
Thursday, September 17. 2009
Today I had a nice WTF moment. I was looking into when gcc is going to print (null) rather than segfaulting on trying to dereference a NULL pointer. I knew newer gcc versions are doing that in some situations. But it turns out this is more complex than I initially thought.
So here we have 5 little test programs:
#include <stdio.h> int main(void){ return 0; }
#include <stdio.h> int main(void){ return 0; }
#include <stdio.h> int main(void){ return 0; }
#include <stdio.h> int main(void){ return 0; }
#include <stdio.h> int main(void){ return 0; }
Now I expected some kind of consistent behaviour at least apart from the last snippet as from the C programming point of view the source does exactly the same. But it seems this is not the case.
The first snippet is straightforward, even in the generated assembler the code dereferences a NULL pointer in puts and therefore results in a segfault. But wasn't it printf from the GNU libc that replaces such cases with (null)? Yes it was but it turns out only in some cases. Now here is the fun part. If we look at the generated code for the first example we see:
00000000004004ec <main>: 4004ec: 55 push %rbp 4004ed: 48 89 e5 mov %rsp,%rbp 4004f0: bf 00 00 00 00 mov $0x0,%edi 4004f5: e8 e6 fe ff ff callq 4003e0 <puts@plt>
Huh? puts? Now that is interesting. It seems like gcc sees the format string "%s\n" and after that a pointer (void *) so it assumes the usage of puts does make sense so it optimizes the call.
Now for the second code snippet this is not the case:
00000000004004ec <main>: 4004ec: 55 push %rbp 4004ed: 48 89 e5 mov %rsp,%rbp 4004f0: be 00 00 00 00 mov $0x0,%esi 4004f5: bf fc 05 40 00 mov $0x4005fc,%edi 4004fa: b8 00 00 00 00 mov $0x0,%eax 4004ff: e8 dc fe ff ff callq 4003e0 <printf@plt>
In this case gcc sees the format string and an integer so it can't just use this with puts in a way that makes sense. printf is used and the result is (null).
Until this point the behaviour is somehow predictable at least if you know that.
But it becomes even more strange. The third and the fourth example both result in the usage of printf and therefore the displayed result is (null). In my opinion it seems that gcc is testing exactly for "%s\n" (as puts prints a newline at the end anyway). So these two examples don't segfault as well. If there's a newline gcc is - or at least that's my impression - already concatenating the format string with the pointer value.
In the last case the newline is present again. However there is a leading string in front of the format string %s. Here gcc is not seeing this as a whole thing concatenating it and calling puts. It's using printf again and results bla: (null).
I have no idea what the reason behind this behaviour is, I guess there are good arguments for that by the gcc people. But honestly, it SUCKS and is highly inconsistent, *grrr*. The whole behaviour isn't even consistent between different gcc versions.
The above results are tested with gcc (Debian 4.3.4-2) 4.3.4. I also tested with gcc (GCC) 3.4.3, in this case all of the above examples result in a segmentation fault (not sure when this (null) replacement feature in the glibc was introduced though). You can also disable this "optimization" by using -fno-builtin-printf btw.
|








